Best Practices Checklist
Are you prepared to protect your firm from cybercriminals?
Be sure to follow these 7 cybersecurity best practices!
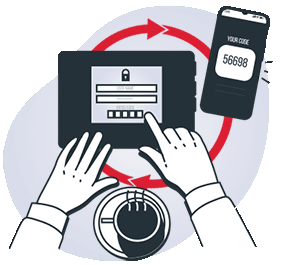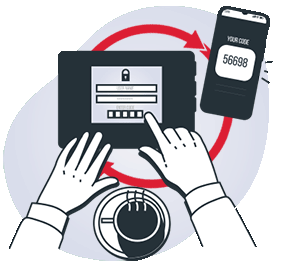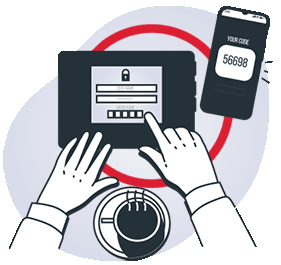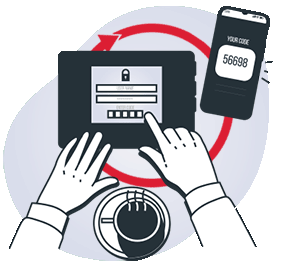

Multi-Factor Authentication
MFA means verifying a user’s identity with two or more independent credentials.
Authenticating with an app or push notification is the safest route.

Phishing Training and Testing
Train users to identify phishing emails and follow correct protocols.
Education combined with testing at regular intervals leads to organizational compliance.


Endpoint Security
Protecting endpoints (desktops, laptops, mobile devices, etc.) is essential, particularly in remote and hybrid working environments.
Fund managers should combine endpoint protection with monitoring and remediation.


Infrastructure Security Monitoring
Monitor security events on essential infrastructure (servers, routers, switches, etc.) to keep production environments running smoothly.
Many firms rely on Managed Detection, Response and Remediation (MDRR) solutions from a reputable provider – such as Linedata.

Vulnerability Assessment
Patch known vulnerabilities in your (often robust) tech stack.
Vulnerability scanning is essential, and the ability to quickly scan, identify and patch vulnerabilities with a proven process ensures even greater cybersecurity.


Security for Office 365
Secure applications within Office 365, which holds a bevy of confidential and sensitive information.
Run assessments and use optimal security settings.

Incident Response
Incidents are inevitable, but having a documented response plan will save you precious time when an incident occurs.
Create documentation that defines roles and actions to be taken by specific representatives.